10/Nov/2017
The cyber kill chain is a method of analysing a threat in a 7-step process:
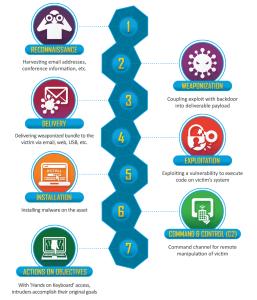
The Cyber Kill Chain (Lockheed Martin)
The cyber kill chain is designed so that victims can stay one step ahead and have provisions in place to stop an attacker, it phases out the different stages of an attack from the attacker’s standpoint so that the victims can have previsions in place to try and prevent an intrusion attempt.
- Reconnaissance – The reconnaissance phase is the first stage of the kill chain where the attacker would gather all evidence they could find from various sources about the target company. Including as many contact emails and numbers which can be used to build a better profile of the target, the better the profile the easier it would be to use for the purpose of social engineering, for example.
- Remediating actions
- To try and prevent the reconnaissance phase, it is best to be aware of any information that is publicly available and to try and limit this information so that it is harder for an attacker to find any information they may need.
- Remediating actions
- Weaponization – The weaponization phase is where the attacker will plan the attack carefully and split the attack into its different phases as well as choose and create a tool that will be used to create the payload by coupling malware and an unsuspicious file such as a Microsoft office file. There are many free tools available that can easily merge malware with common files.
- Remediating actions
- To try and prevent the weaponization phase is essential to log and record any malware or attacks on the system including any files and metadata so that any new attacks can be cross referenced to try and find similarities so that any repeat attackers can be easily picked up and similar malware can be found.
- Any malware logs should be shared with any competitors so that attacks can be used to identify specific tools and keep up with any advancements in terms of tools from attackers, by having a shared log or at least communication between companies in the same sector it can be ensured you are always a step ahead of any attacker.
- Conduct a detailed malware analysis and understand how it was made and what it’s intended purpose was.
- Analyse the timescale of the attack from when the malware was created to when it was used, this can be useful to identify whether it was a generic attack or specifically targeted to an individual part of the organisation.
- Remediating actions
- Delivery – the delivery phase is where the attacker decides how he wants to distribute the malware and through what method, this can be through a phishing email or through something simple such as leaving USB’s lying around. The phase is where the deployment is seen most effective and what method as simple methods can be extremely effective if a good security methodology is not implemented within the company.
- Remediating action
- The delivery phase is the first opportunity to block any point of attack, it is important that an attack is prevented at this first phase as it is the least impactful phase.
- It is important to understand the target of attackers and who was targeted and at what time they were targeted as all of this information is relevant, the human aspect is considered the weakest point of the kill chain, for example an attack in a phishing email on a Friday evening to the right target is far more likely to be successful than one on a Monday morning.
- It is important to implement a security methodology within the company as implementing a system and educating staff can strengthen the human aspect of the kill chain, this can be especially effective by using the same tools of the attacker by using a phycological aspect, Using the nudge theory for example, by rewarding employees for good practices. Or by having a few people comply could start an effective case of group conformity to the idea of security where employees start complying as it has become the “norm” with the rest of the employees.
- Remediating action
- Exploitation – The exploitation stage is the stage where the exploit runs and launches the exploit itself to get intended actions such as keylogging or packet capture. These exploits are normally deployed through malicious emails or exploits known as “Zero Days” which can be purchased online in vulnerability black markets or found themselves.
- Remediating action
- To defend against the exploitation phase, it is again important to have a good security policy and conduct regular staff training.
- Conduct secure coding training for any web developers.
- Conduct regular vulnerability scans and penetration tests.
- Implement endpoint hardening measures such as using Microsoft EMIT.
- Remediating action
- Installation – the installation phase is where the exploit will install a backdoor to the system where the attacker uses the vulnerability found to inject their malware, the exploit will be used to execute commands to install a webshell or backdoor to the system in a way It can lay dormant and undetected for a period of time and are sometimes disguised to look like part of system files.
- Remediating action
- To implement Intrusion Prevention and Detection systems.
- Using endpoint security software to log and detect any activity
- Understand the level of user permissions required by each user and look for anomalies.
- Analyse abnormal files and extract certificates of executables.
- Understand the compile time of malware.
- Remediating action
- Command & Control – The command and control phase is where the tool takes control of the user’s system it is attacking while running silently, it aims to execute while laying undiscovered for the longest period of time while enabling remote connectivity for the attacker.
- Remediating actions.
- Identify the control of the system via the network traffic being sent by analysing packet capture.
- Network hardening – check open network ports, require proxies for traffic.
- Network adversary search.
- Customize and clean up blocks of C2 protocols on web proxies.
- Remediating actions.
- Actions on objectives – The actions on objectives is the last phase where the exploit is in place and running for its intended purpose without being detected for as long as possible while ex-filtrating high value data, such as collecting user credentials, privilege escalation or even to overwrite or corrupt company data. Anything that happens can be unpredictable as it is now down to the attacker.
- Remediating actions
- To implement the incident response playbook
- Detect data exfiltration, lateral movement or unauthorised credential usage.
- Network packet capture to re-create an incident
- Conduct impact assessment
- Remediating actions
The best way to dispute your risk is to analyse your system to identify the companies most valuable assets and split funds to protect these key areas of your organisation, these most valuable assets can be clearly identified by finding the maximum tolerable period of disruption of the service which equates to how much loss it would equate to.
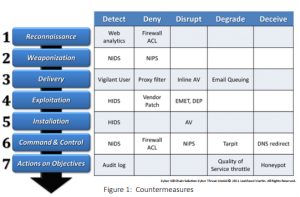
The below diagram can show what countermeasures can be put in place to block/disrupt or deceive each phase of the kill chain to try and make it harder for any attacker.
To build a good level or resilience it is useful to store and analyse by recreating and testing incidents again to harden your system.
Author: Taran Ranger, CyNation
