29/Sep/2017
Who are Equifax?
Equifax Is a consumer credit reporting agency that holds the information on over 800 million individual consumers and more than 88 million businesses worldwide, this equates to Equifax holding information of around every person in Europe and more, due to the nature of the industry Equifax hold all types of sensitive data ranging from Names, Housing history, Social security numbers and income.
What did the breach consist of?
On September 7, 2017 Equifax announced it had suffered a major data breach, around 143 million consumers in the United States, UK and some Canadian resident’s personal data is presumed to have been compromised.
It is currently assumed to be caused by an exploit in the open source Apache Struts framework named CVE-2017-9805, the exploit allowed arbitrary code execution. This is the case as the REST Plugin XStream that Struts is based on is triggered as the program insecurely deserializes user-supplied input in XML requests.
Based on research firm Imperva’s analysis on the Apache Struts plugin, “the problem occurs in XStreamHandler’s toObject () method, which does not impose any restrictions on the incoming value when using XStream deserialization into an object, resulting in arbitrary code execution vulnerabilities.”
This specific vulnerability was publicly announced on 09/04/2017 along with new Struts Framework software releases to patch this and other vulnerabilities so at the time of the breach would have been a Zero-Day-Exploit at the time of July, the exploit could have been self-discovered or bought on the vulnerability black market.
Why is the data breach significant?
The breach is particularly significant as although it is not among the largest high-profile breaches it does however contain some of the most sensitive information and holds a very complete profile of its customers allowing for the information to be used for identity theft and holding great value for black market trading.
How was the way the response was handled significant? & what does it tell us about Equifax’s approach?
On September 7, 2017 when Equifax announced it had suffered a major data breach, and they also reported the breach occurred in mid-July. Equifax confirmed they knew of the breach but were dealing with the situation and in the process of notifying the regulatory body of the ICO.
The response here is questionable as when a breach is discovered it is common law in certain US states that the body is notified with “Undue delay” or within a certain time frame, the 5-6 week period between when the breach was discovered and the response statement with no clear process or systems in place for customers to voice their concerns and also “in the process of reporting” the ICO of the breach seems like there was no system or contingency plan in place for this type of situation, as well as this their security processes are called into question where there is no clear adherence to any common security framework where processes would be in place to deal with incidents and contingency plans would be put in place.
Equifax’s further actions further this point as their response was to setup an unsecured WordPress site for users to check if their personal data was safe, the site was firstly unsecure requesting a social security number to check the account causing confusion if the site was simply a phishing attempt in itself.
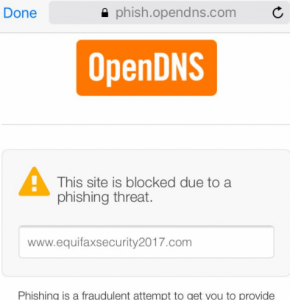
Figure 1: Insecure Site Notification
The website has also been under fire for not providing accurate information but instead providing a generic response stating “Your personal information may be at risk” and offering a year free identity theft protection and credit file monitoring. This has been tested by numerous reports online and no matter what is entered, there is no input validation required, the same message appears.
The last point is Equifax is trying to stop any legal action in the way of including a compulsory terms and conditions to check that your data is safe on their website and accept the free identity theft protection and credit file monitoring, you also agree to opt-out of any legal proceedings.
The actions Equifax has taken have led to not only financial loss but also reputational damage, while also losing the trust of many customers and maybe even partners, the blame does not only lie with how the incident was managed but also on any third parties associated with Equifax, to protect a company’s assets it is important that not only your own organisation is protected with the right policies and security frameworks in place, but also auditing any third parties as they may highlight a single point of failure that is often missed, and in this case was detrimental.
What should have Equifax have done & how would the GDPR have helped manage this?
Simply Equifax were guilty of basic negligence, and this is common practice with many organisations at present, who may be unaware of their obligations or just inexperienced, as personal information is deemed so valuable in the modern day the laws in Europe are due to be updated, this comes in the form of the GDPR that comes into force on the 25th May 2018.
The GDPR takes precautions to make sure organisations are properly prepared for any data breach and have necessary measures in place to deal with every step of cyber resilience from protecting yourself from a breach to business continuity measures and incident response, the regulation requires a security framework to be put in place as well as security policies, these if properly adhered to should point out any single points of failure and require security review audits for internal and external operations, as well as regular patch management which in this case was ignored as a fundamental aspect of security framework. The GDPR aims to ensure personal identifiable information is protected and not misused by organisations while giving users back control over their own data, it therefore requires organisations to notify the ICO and customers of a data breach within 72 hours of discovering the breach.
To conclude had the GDPR already have been in place following all the mentioned breaches based on a 2016 operating revenue of $3.145 billion, Equifax may have been fined for non-compliance which would equate to 4% of their global gross revenue and a further 2% for other individual breaches of responsibility that would be fined at 2% such as data processing, handling and to implement technical and organisational measures to ensure data protection by design and default (Article 25) and finally 2% to report breaches when required by the GDPR to do so (Articles 33-34).
The GDPR does state that in cases where the same or linked processing involves violation of several provisions of the GDPR, fines may not exceed the amount specified for the most serious infringement. But take note of the fact that the fines do apply per individual breach.
Under these provisions Equifax could be fined 4% + 2% = 6 % of their global gross revenue equating to around $94.4M.
Equifax Argentina
On the 13th September 2017, a further vulnerability was discovered by Cyber-crime blogger Brian Krebs, His report highlighted that a regional branch of Equifax in Argentina has again neglected basic security issues, where a online employee tool used to store customer data had the simple username/ password combination of Admin/Admin highlighting again that a security ethos or framework is not in place.
If this vulnerability has been used maliciously and had resulted in another data breach the same fines could again apply.
Author: Taran Ranger, CyNation
