22/Sep/2017
What is Locky?
Locky is a form of ransomware which first appeared back in 2016. Locky originally was delivered by email, usually looking like an invoice requiring payment. Most of the emails are designed to play on human curiosity. Emails as simple as “please find the documents attached, Thanks” get users downloading the file to see what is attached without thinking.
The downloaded document tries to convince the user to enable macros which are usually disabled by default (The bellow example is a pretty simple attempt). Enabling macros will enable Locky to encrypt their files. For example,
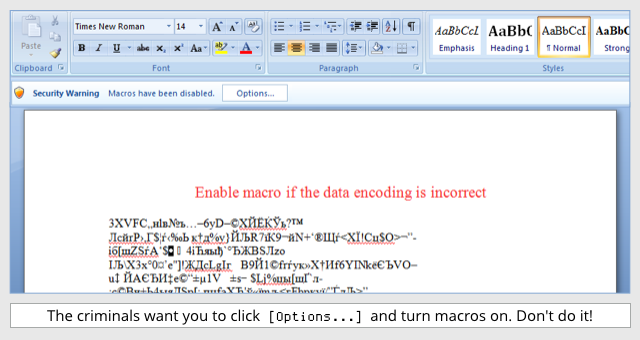
Researchers have discovered two new major versions of Locky being distributed via voluminous malspam campaigns. One researcher found 62000 emails containing Locky within a 2-day window. The first variant to emerge is a version called Diablo6 and the second variant is called Lukitus. There could be numerous reasons for its return, one reason might be down to the popularity of Wannacry and NotPetya ransomware. They caught everyone’s attention with many then downloading the latest patches to stop the spread of it. Locky spreads via email and uses social engineering rather than an unpatched exploit to spread. Therefore, Locky might currently be more effective for the cyber criminals.
What can you do to protect against Locky?
It is good practice not to open links or download attachments from emails that you do not recognise, as Locky and other malware spread via people downloading or clicking on malicious links.
Other things to consider:
- Backup regularly and keep a recent backup copy off-site
- Useful just in case Locky does encrypt your files, you can just restore from your backup.
- Don’t enable macros in document attachments received via email.
- Macros aren’t enabled by default so criminals try to convince users to enable them through various social engineering techniques. (an example is shown above)
- Consider installing the Microsoft Office viewers.
- Macros don’t work in office viewers, meaning Locky won’t be able to encrypt any files.
- Always keep software up to date
